The Likelihood of Occurrence and Identifying Viable Threats to Business Continuity

Threat Assessment Template
Identify the threats that will have the biggest impact on your organization.
From cyberattacks to workplace violence, businesses today face nearly constant threats from a variety of sources. And the COVID-19 pandemic, the rise of remote work, and a web of other risk factors are only making it harder to identify and respond to these threats.
Over 800,000 cybercrimes were reported in 2021, a 7% increase over 2020 and an 81% jump when compared to 2019. The dramatic increase in remote and hybrid working means business continuity and threat assessment teams must also rethink their risk management strategies to protect employees across varied work environments.
Below, we'll provide a framework for conducting a business threat assessment and discuss how the threat assessment process can be used to protect your employees, facilities, and critical infrastructure. We'll also explore tools—like a fill-in-the-blank threat assessment template—and strategies for more effectively monitoring, identifying, and communicating about threats that may impact your organization.
What Is a Threat Assessment?
Sometimes called a risk assessment—a threat assessment is a process for evaluating the impact and likelihood of perceived threats. And it is an important part of risk management. What makes it somewhat challenging to define is that the term "threat assessment" has multiple meanings. From corporate security to school safety, the phrase can be used in different contexts:
- Cybersecurity threat assessment: IT and information security teams perform cybersecurity threat assessments to identify potential vulnerabilities and security gaps. Findings from the risk assessment are used to develop strategies to protect against data breaches, targeted attacks, and other technology-related security risks.
- School threat assessment: According to the National Association of School Psychologists, "threat assessment involves determining whether a student poses a threat of violence." School districts and educators use a behavioral threat assessment as a critical part of school safety and violence prevention strategies. Developed in collaboration among school staff, school administrators, law enforcement, and mental health professionals, the purpose is to identify potential threats of future acts of violence from students. By analyzing key risk factors—such as a history of threatening behavior—school officials can develop intervention plans and safe school strategies.
- Organizational threat assessment: A business threat assessment is typically performed by a cross-functional team composed of representatives from different parts of the business. The purpose is to identify and evaluate all of the events—from severe weather to supply chain disruptions to violent behavior—that can adversely affect personnel, operations, or critical assets.
This article focuses on organizational assessments of risks to employee safety and business continuity. With the information gained from a business threat assessment, your organization can develop risk mitigation strategies to protect employees, business operations, and facilities from potentially dangerous or disruptive events.
Looking for more guidance on how exactly to put this together? Check out our comprehensive threat assessment template.
Identify your business' most critical threats with this fill-in-the-blank template.
Building Your Threat Assessment Team
Often spearheaded by an organization's business continuity or risk management function, a threat assessment team should include representatives from a variety of departments across your organization that have a role in safety and security. At a minimum, it should include some executive, human resources, and facilities management team members.
The threat assessment team will convene to identify, evaluate, and develop prevention and mitigation strategies for various threats your business may face. It may also be necessary to include external stakeholders and partners who may play a role in emergency response efforts, such as local law enforcement officials and mental health professionals.
4 Steps to Conduct a Business Threat Assessment
With your threat assessment team established, it's time to get to work. Here are the four iterative steps to conducting a business threat assessment:
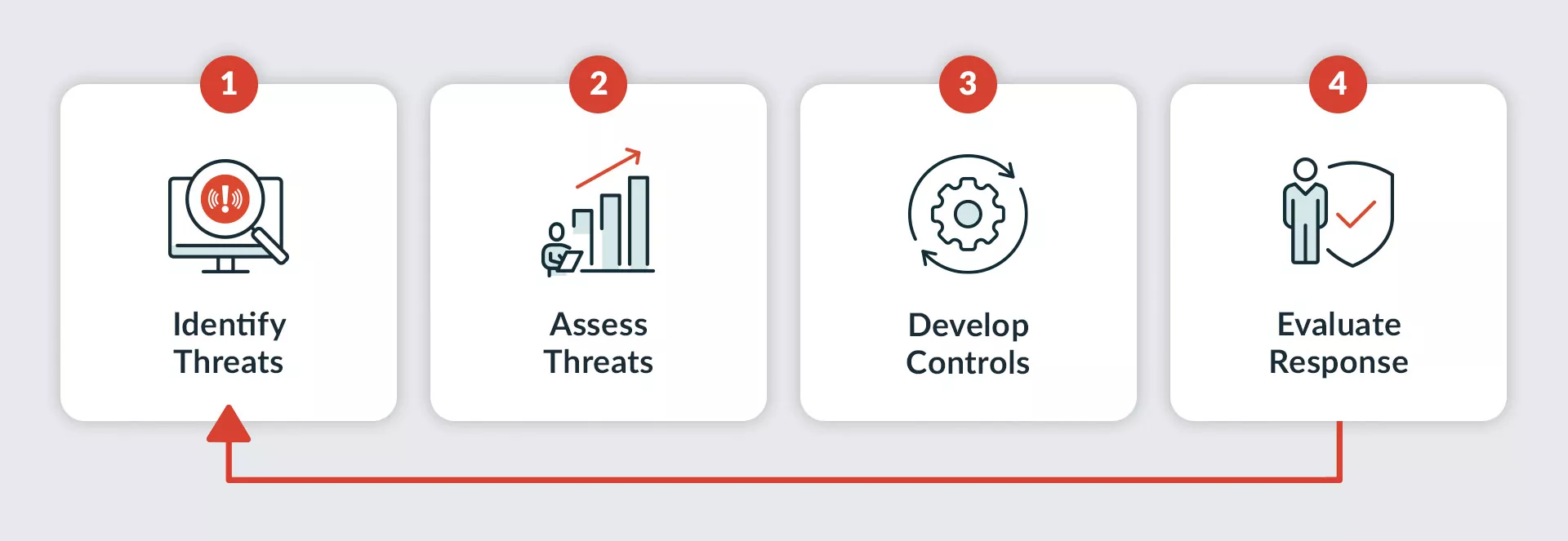 Business Threat Assessment Cycle
Business Threat Assessment Cycle
Step 1: Identify threats
The first question you need to ask is: What are the threats? Make sure you are aware of the broad array of hazards that could impact your people and assets. We have listed some threat assessment examples related to both external and internal risks.
External threat examples
- Meteorological: Hurricanes, severe thunderstorms, blizzards, tropical storms
- Geological: Earthquakes, wildfires, tsunamis, landslides, floods
- Biological: Disease outbreaks, pandemics, illnesses
- Transportation: Significant road closures, widespread flight delays
- Communications: Cell coverage outages, power outages
- Violent acts: Active shooters, civil disturbances, bomb threats
Go through the types of threats listed above and ask yourself: How would this impact my organization?
To answer this question, consider the nature of your business and work environments. If you are a software company with just one office located in Texas, for example, your risks will look substantially different than those of a large manufacturing company with offices scattered around the northeast.
Make sure you also take into account remote workers and traveling employees. You have a duty of care to keep your employees safe, no matter where or how they work. Using a threat intelligence solution can help you proactively monitor and communicate about all external threats, including those that impact your remote and mobile employees.
Internal threat examples
- Information technology: Internet outages, systems downtime, corrupted data
- Utility outage: Electrical power, water, sewage, air conditioning/heating
- Supply chain interruption: Supplier failure, transportation interruption
- Accidents: Workplace accidents, structural collapse, mechanical breakdown
- Hazardous materials: Chemical spill, gas leak, radiological accident
Whereas external threats require you to monitor wider variables, internal threats are often more readily apparent. Some internal threats are universal (e.g., Wi-Fi outages), but most are company-specific. For example, you might look at your supply chain and ask yourself: Where could things go wrong? If your operations involve hazardous materials, make sure you have a hazmat safety plan in place. If your office building has a set of stairs prone to accidents, put up a sign warning people to "watch your step."
Assessing internal threats requires a comprehensive risk analysis of your business, from facilities to supply chain to personnel. Using the bulleted list above as a starting point, consider which threats impact your operations—and how.
Step 2: Assess threats
Once you have identified the threats to your business, you need a way to evaluate the impact and likelihood of those threats. These further assessments go hand in hand to determine the overall risk level.
A risk matrix—also called a probability matrix or impact matrix—can be useful for performing this threat assessment. The matrix helps assess each threat based on 1) the likelihood that the threat will occur and 2) the potential impact the threat will have on your business.
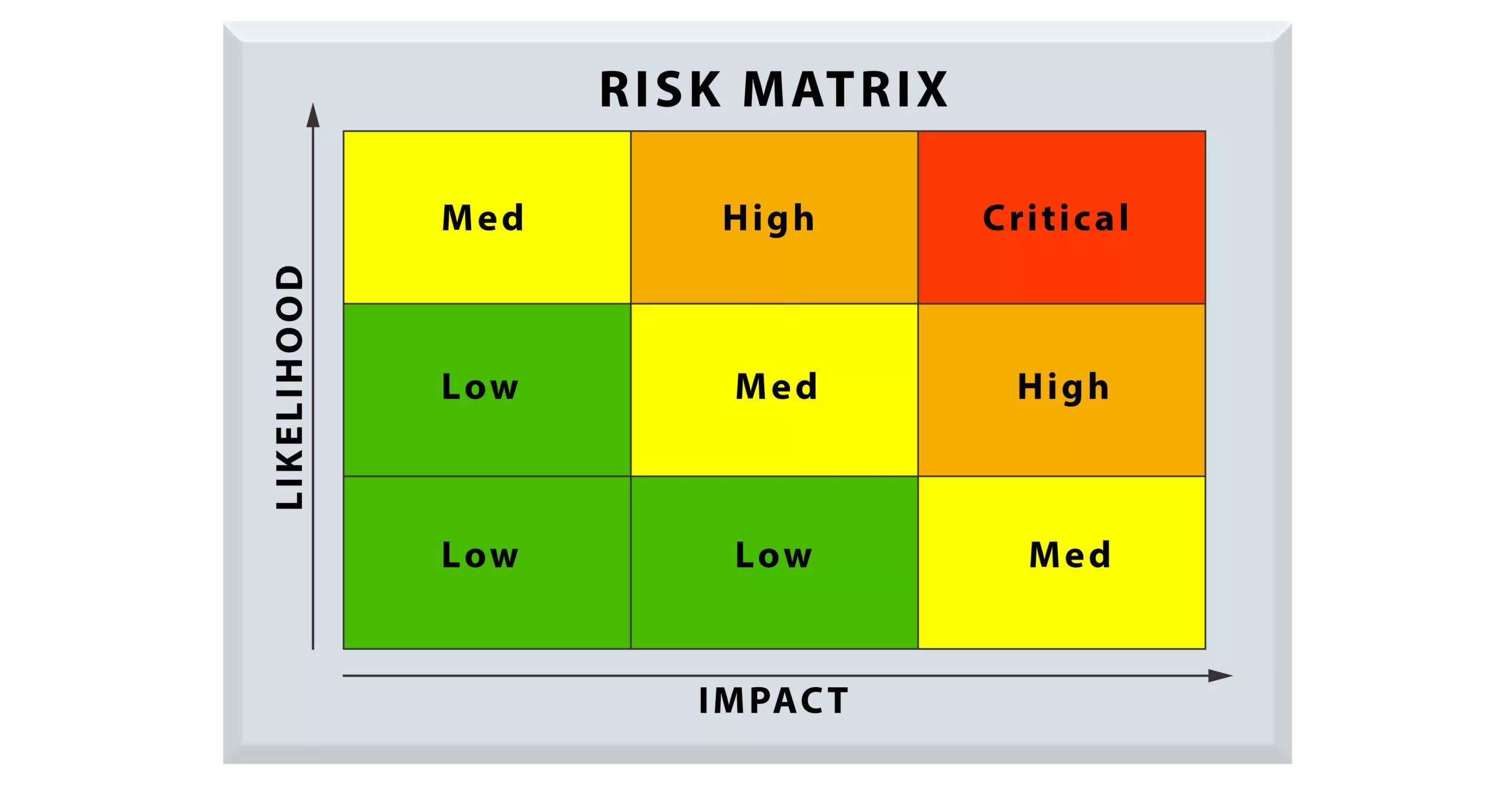 Risk Assessment Matrix
Risk Assessment Matrix
Likelihood
Certain factors increase the likelihood of a threat occurring. Location and past history are both important risk factors to consider when evaluating the probability of a threat. When completing a risk assessment matrix, the likelihood of the threat occurring is often ranked on a five-point scale from improbable to frequent.
A company in California, for example, has a far greater chance of being impacted by an earthquake or wildfire than a company based in New England. Similarly, a company in a major metropolitan city is more likely to be affected by civil disturbances than one in a sleepy suburban town.
It's common for large companies to have many office locations across the country, even across the world. Each of these locations has its own set of potential threats. With many employees now working remotely as a result of the coronavirus pandemic, employers must consider all of the locations employees work from—not just where the company's facilities are located.
Impact
The impact of a potential threat is the amount of damage or harm the threat could create. On a risk assessment matrix, the severity of a threat is often ranked on a four-point scale from negligible to catastrophic.
When assessing threats, consider all the different types of impact. You can think of impact in three broad categories: people, locations, and assets. From employee safety to financial loss to reputation harm, a threat can negatively affect your business in a variety of ways.
Consider these two different threats as examples for assessment: 1) the threat of a winter storm and 2) the threat of your CEO dying. The first threat has a medium impact but a high likelihood. If you're located in the northeast, winter storms are essentially guaranteed—but they shouldn't derail your business. The second threat, on the other hand, has a high impact but a low likelihood. It is highly unlikely that your CEO will die suddenly—but it would have a huge impact. During this analysis, you might conclude that a winter storm is high-risk, whereas the CEO dying is medium risk.
Obviously, risks will change over time. The likelihood of a winter storm is nil in July, so there is almost no risk to your business. An upcoming executive trip to a dangerous foreign city, on the other hand, might raise the likelihood (and risk level) of your CEO getting injured.
Document your analysis of each threat's likelihood and impact in a methodical way, like with our threat assessment template.
Step 3: Develop controls
Once you have identified the potential threats and you have a way to quantify the impact, you need to plan your response. This means implementing controls that mitigate the threats you've identified.
You will want to look at your overall risks and decide which actions you and your business can take to reduce each overall risk. For most risks, this means both:
- "How do we decrease the likelihood this will happen?"
- "How do we decrease the impact if this does happen?"
If you're a business in Chicago, for example, you are basically guaranteed to face a winter storm. While there is not much you can do to prevent a storm from happening, you can minimize the disruption that a winter storm will have on business operations—the impact. On the other hand, if employees must work or travel in a region with high crime rates, you may want to focus on reducing both the likelihood and the impact of safety threats to your people.
Regardless of the risk, here are a few specific controls you should plan on implementing:
Train employees
The first and most basic control in business risk management is employee training. Risk mitigation can't just exist in one department or one person. Although it may start in your business continuity and disaster recovery (BC/DR) division, it can't end there.
Make sure that your entire organization knows what the plan is—especially for high-likelihood threats. Often, the most effective employee training involves active participation. Most companies conduct fire drills, which is good. But you shouldn't stop there. Consider the wide range of tabletop exercises your company can implement to offer practice for various threats.
Create policies
In addition to training employees, create threat assessment procedures and guidelines to mitigate the identified threats. For example, in the event of a severe winter storm, you'll want a policy in place for how employees are notified of delays or closures. And to keep traveling employees safe from the variety of threats they may encounter, you'll want a comprehensive corporate travel policy.
Your threat assessment procedures should indicate when third parties—such as law enforcement or mental health services—need to be involved. For example, when threats of violence arise, it is necessary to report them to and involve local law enforcement officials.
Document emergency response plans
As every emergency management professional will tell you, the best time to prepare for an emergency is well before it occurs. By creating an emergency response plan—a documented series of steps your organization will take during an emergency—you can help ensure employee safety and minimize the impact on critical operations.
Emergency response plans help organizations address various threats, such as hurricanes, wildfires, winter weather, chemical spills, disease outbreaks, and other hazards. The goal is to reduce or prevent human injury and property damage during threatening situations by documenting the steps that can ensure a timely response tailored to each scenario.
Step 4: Evaluate your response
The final step in a business threat assessment is what makes the process iterative. Once you have identified a threat, assessed its impact, and responded, you need to assess your response.
Here are the questions you need to be asking:
- Was this a threat our organization had identified?
- Did we properly assess the likelihood of this threat?
- Did we properly assess the impact of this threat?
- Was this threat avoidable?
- What controls did we have in place for this threat?
- How effective were our controls?
- How quickly were we able to respond?
- Was our communication effective?
- Did we have the proper resources to address the threat?
Once you have answered these questions, it's time to turn to the big question: What can we do better? You will never have the perfect response to a given threat. Even when you execute your plan down to the letter, look for ways to improve your plan based on how it worked. Don't let good be the enemy of great .
Talk to employees—especially those directly impacted by the threat. By soliciting employee feedback, you can uncover weaknesses in your plan that may have otherwise gone unrecognized. One effective way to conduct this follow-up is to send out an employee survey. Your employees will likely have ideas for ways you can better prepare them for the threat or better respond.
Once you have evaluated your response and how it could be improved, go back to Step 1. Repeat the process, integrating the new relevant information and feedback you have received.
"There is a high volume of critical incidents happening around the world every day. The volume of information available to businesses is incredible, and being able to sift through that raw information to find meaningful insights takes expertise." —Sara Pratley, VP of Global Intelligence, AlertMedia
Taking Advantage of Threat Intelligence Technology
A proper business threat assessment requires modern technology to support it. You can't expect to monitor the expanse of potential threats manually—especially when you have remote workers, multiple office locations, and traveling employees. Today's workforce requires the newest technology when it comes to threat monitoring and emergency communication.
Using a modern emergency communication solution with integrated threat intelligence will take organizational resilience to the next level. Your business threat assessment is incomplete without it.
With AlertMedia's emergency communication and threat intelligence software, you can easily monitor and notify employees about emerging threats that may impact them. Using comprehensive threat data from analysts, social media, and news outlets worldwide, AlertMedia performs over 100 million calculations daily to cross-reference the location of each global threat against employee and asset locations. This analysis allows companies to easily see the threats that impact their business.
Let's say a hurricane is in the forecast for the Gulf Coast. Quality threat assessment engines quantify the impact of the threat (identifying which employees and offices are in the path of the storm)—and automatically update this impact assessment as the storm changes. Perhaps you have offices and remote employees in multiple locations near the Gulf Coast. As the path of the hurricane changes, real-time threat intelligence and impact assessments help you rapidly identify those in harm's way to ensure they are informed and prepared.
If a situation requires personalized attention from experts, solutions that allow you to communicate directly with intelligence analysts can give you and your team a responsive, real-time resource when things get hectic. They can answer your specific questions and proactively keep an eye out for additional information, ensuring that you can act on details that are accurate, up-to-date, and relevant.
Combined with powerful emergency communication capabilities—such as survey notifications, event pages, and multichannel messaging—systems such as AlertMedia enable organizations to proactively identify, mitigate, and respond to any threatening situations that may arise.
Strengthening Your Risk Management Approach
While nobody likes to think about facing a threat that could jeopardize their people and business, threat assessments play a vital role in protecting your employees and operations. Conducting a business threat assessment will put your organization in the best position to respond to whatever threats come your way.
In a word, your company will be resilient. You will have an answer to even the most uncertain scenarios because you will have a plan in place ahead of time. With a comprehensive organizational threat assessment—backed by modern emergency communication and threat intelligence technology—you can strengthen your risk management and emergency preparedness capabilities to be ready for any emergency that may arise.
Download Our Threat Assessment Template
Identify the threats that will have the biggest impact on your organization.
Source: https://www.alertmedia.com/blog/business-threat-assessment/
0 Response to "The Likelihood of Occurrence and Identifying Viable Threats to Business Continuity"
إرسال تعليق